Fine Beautiful Tips About How To Detect Rogue Dhcp Server

We need to capture dhcp packets coming from the.
How to detect rogue dhcp server. I'm running epo 5.1.1 and rogue sensor 5.0.1. Log onto your tool’s interface and find settings (or the system equivalent) find alert rules; What you’re looking for is the mapping between the ip address and the physical (mac) address.
Tried waking agent, running client task. Are there are many utilities out. I am surprised that this exercise we do in class still proves to be helpful as well as quite popular.
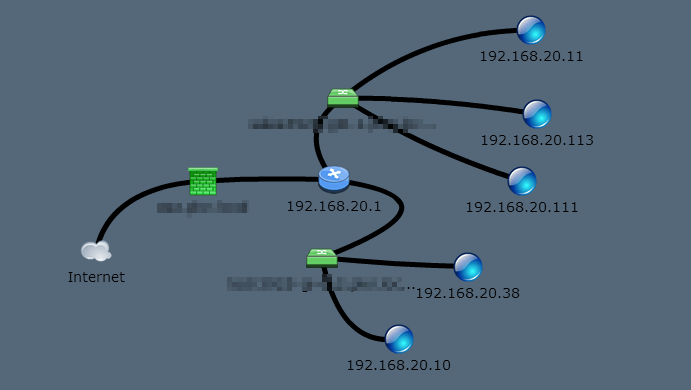
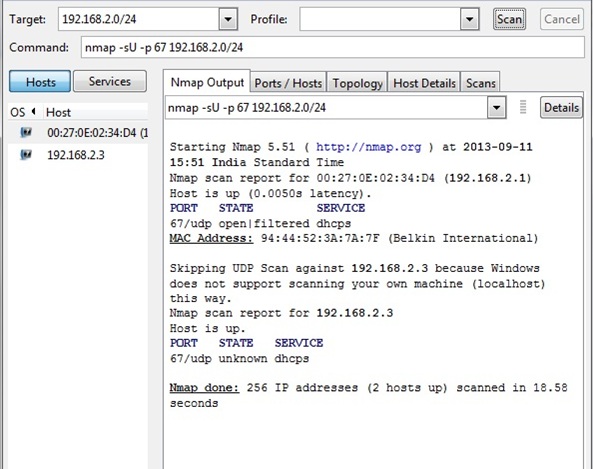
Finding the rogue dhcp server with wireshark. The dhcp server information is usually in /var/log/messages. The malware sitting on 192.168.20.11 sees the dhcp discover flag and is first to respond with a dhcp offer.
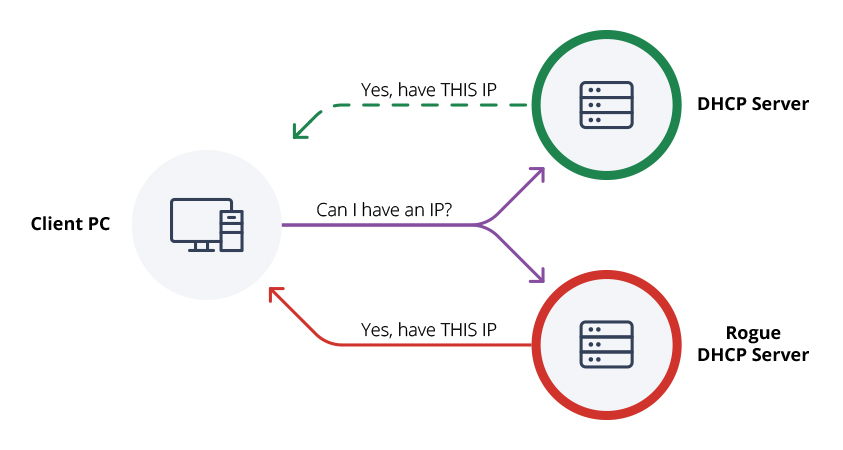
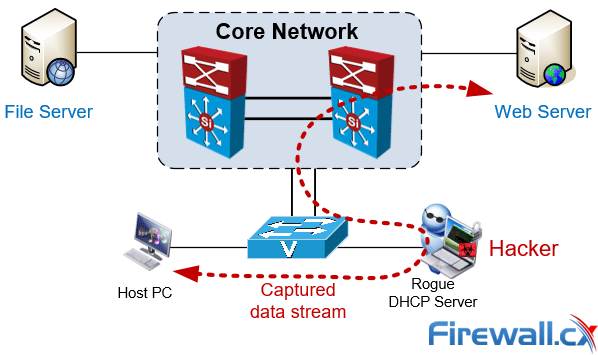
In this step both of the dhcp server will send an offer. You can do this with most configurable. A rogue dhcp server on a network is one that is not under the administrative control of the network staff.
Assign a name to the rule, like ‘rogue dhcp servers’ select. Learn mikrotik routeros tutorial series (english)a rogue dhcp server is a dhcp server on a network which is not under the administrative control of the netwo. One of the most commonly used ways to identify a rogue dhcp server is to turn off the legitimate server.
Give show arp | in 192.x.x.x. One more solution.try continuous ping to the rogue ip from ur laptop that got the dhcp ip.log into the switch on which the laptop is connected. Connect your computer to the network and launch wireshark.
Meraki devices provide mechanisms that will assist in discovering and tracking down the location of a. The pc that made the request receives the new ip. Our aim is to obtain the rogue dhcp server’s mac.
Download networksecurity’s dhcp explorer directly from us. Ip address physical address 10.1.1.1. The most effective way to track down a rogue server is via its mac address.
There are a few free tools to locate dhcp servers on your network, including:
![Detect Rogue Dhcp Server With Wireshark [Step-By-Step] | Golinuxcloud](https://www.golinuxcloud.com/wp-content/uploads/wireshark-461.jpg)




![Detect Rogue Dhcp Server With Wireshark [Step-By-Step] | Golinuxcloud](https://www.golinuxcloud.com/wp-content/uploads/wireshark-454.jpg)




![Detect Rogue Dhcp Server With Wireshark [Step-By-Step] | Golinuxcloud](https://www.golinuxcloud.com/wp-content/uploads/wireshark-463.jpg)


![Detect Rogue Dhcp Server With Wireshark [Step-By-Step] | Golinuxcloud](https://www.golinuxcloud.com/wp-content/uploads/wireshark-467.jpg)