Beautiful Work Info About How To Control A Botnet

Typically for a bigger botnet, a.
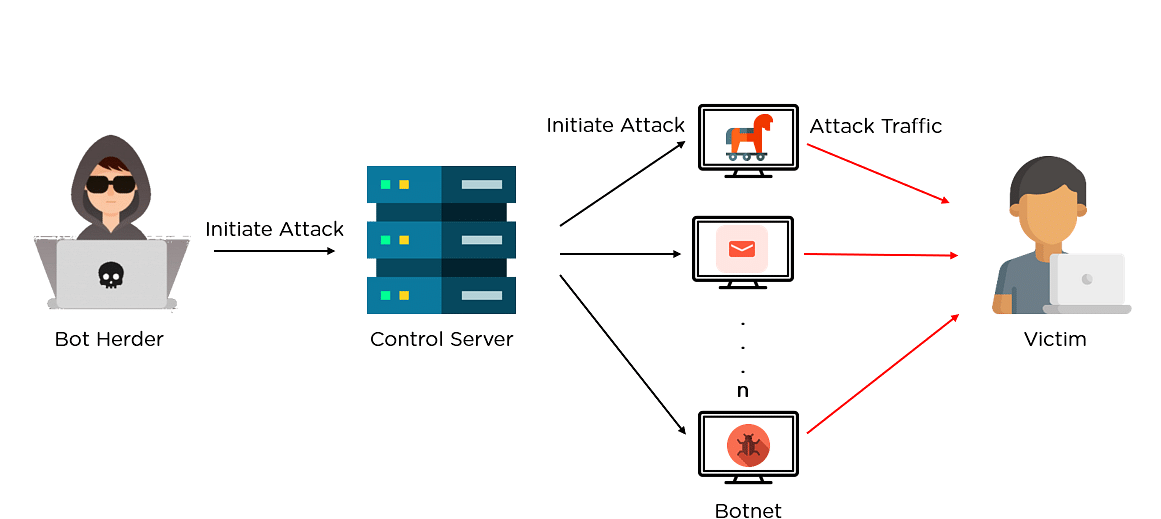
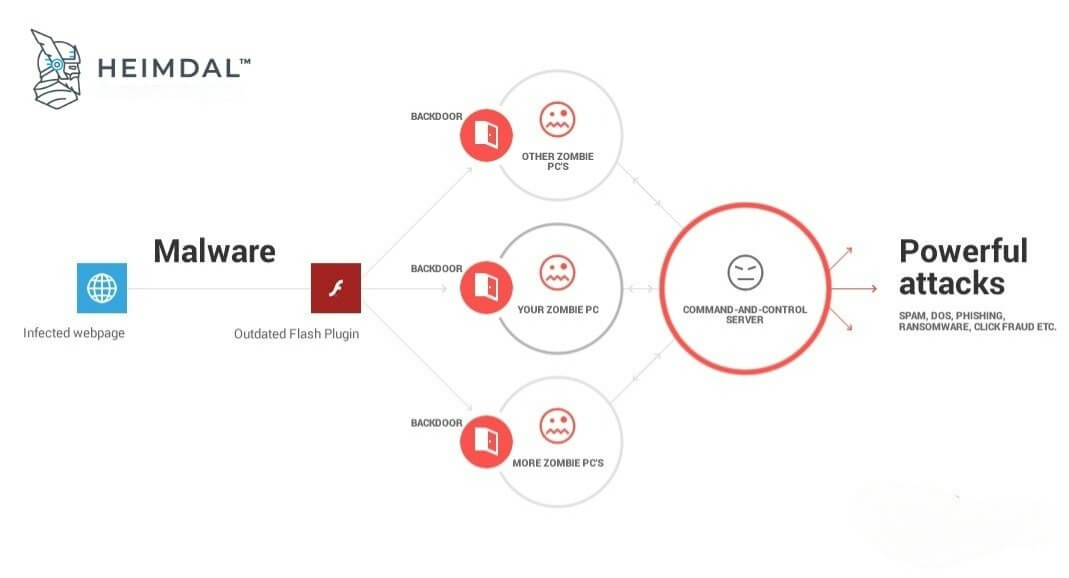
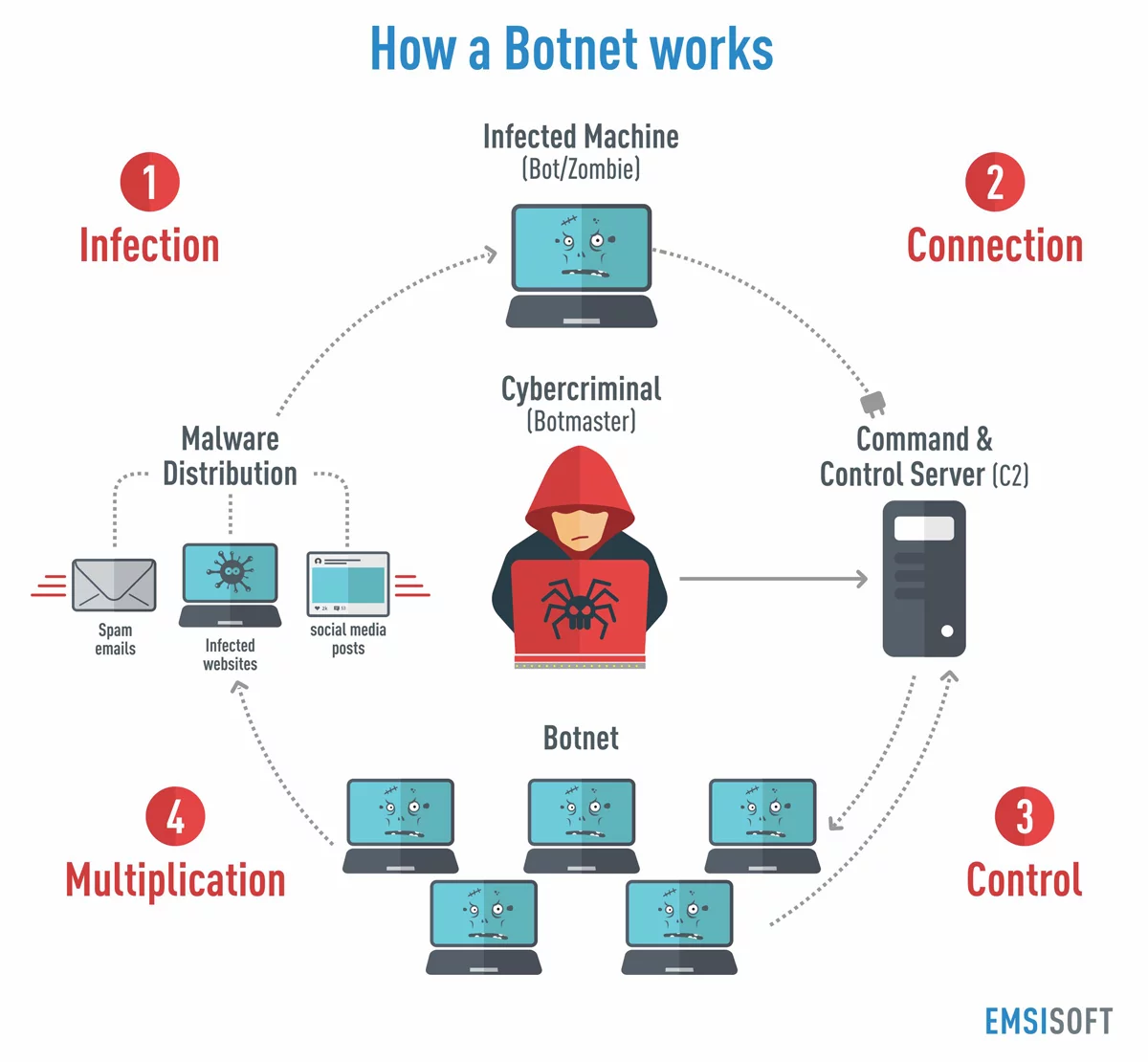
How to control a botnet. Eliminate infection on individual devices. Typically link back to a command and control (c&c) server. This video is part of the udacity course intro to information security.
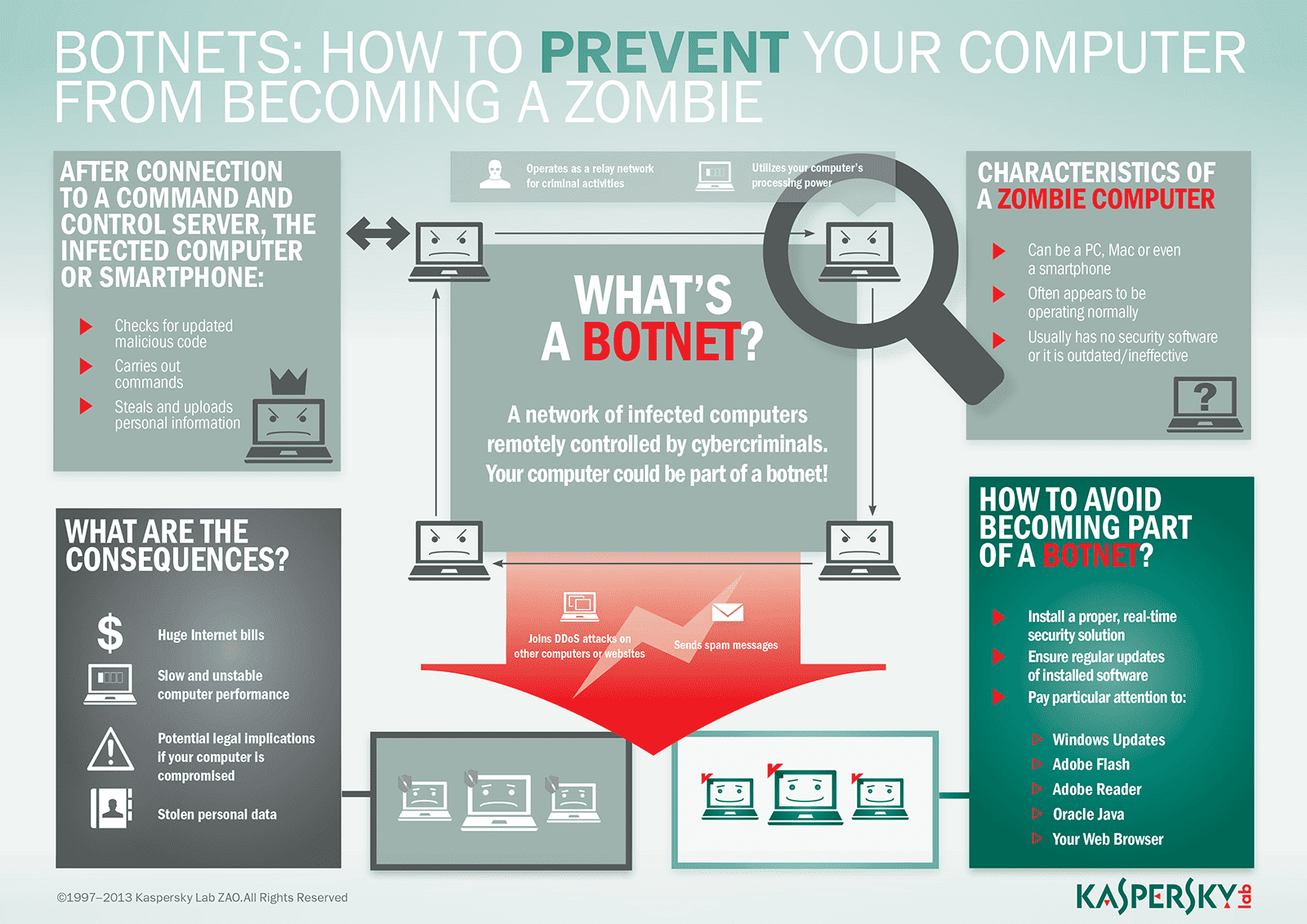
Botnets have often relied on security flaws that have been widely recognized for years, but haven’t been universally patched. Before we get to best practices in botnet detection, let’s do a quick review of exactly what a botnet is. You can stop botnet attacks running on the command and control model by disabling access to the central server which works as the main resource for the malware.
Up to 20% cash back how do hackers control a botnet? 1) a.txt file that will help you set up the channel required for callback. 2) a builder file with the.exe extension, that is required for the compilation of the.
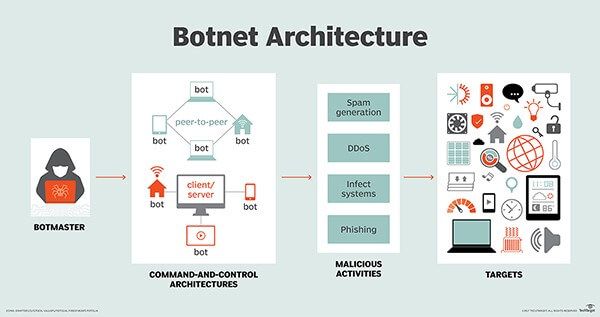
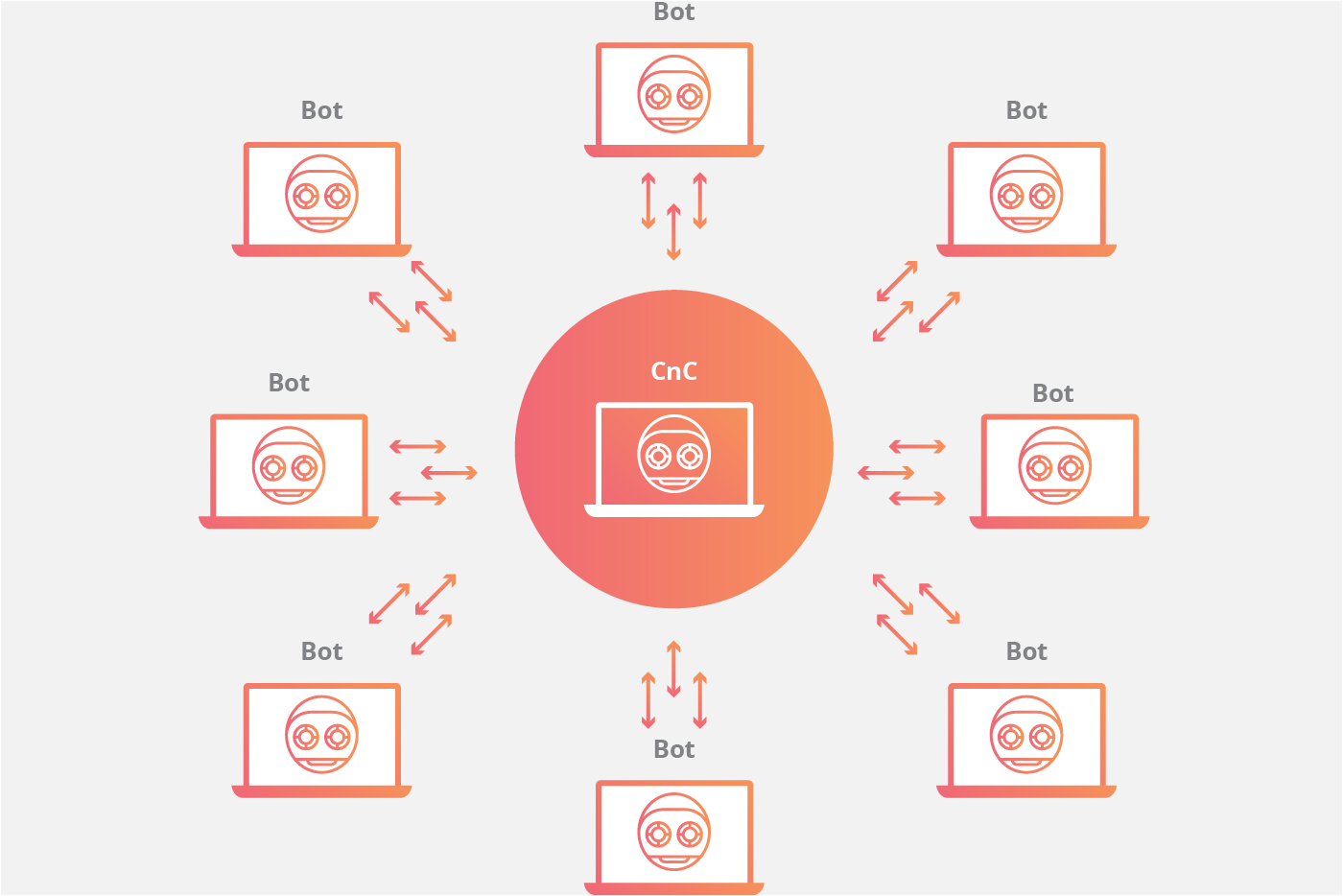
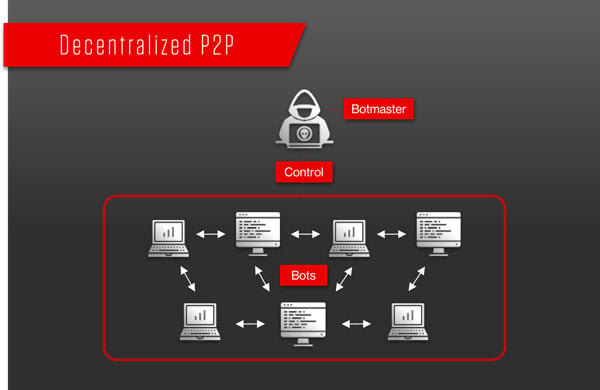
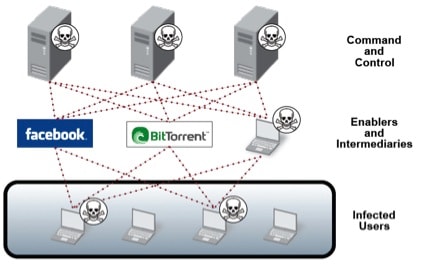
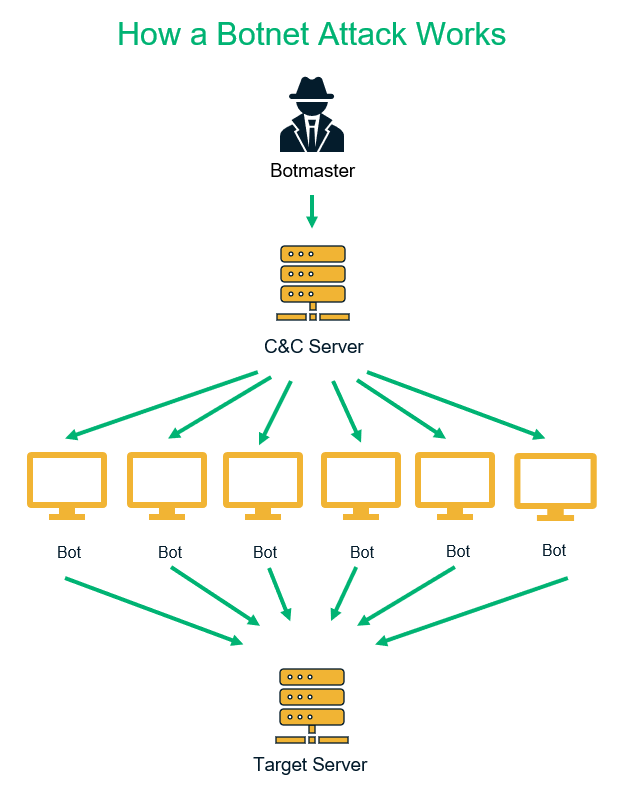
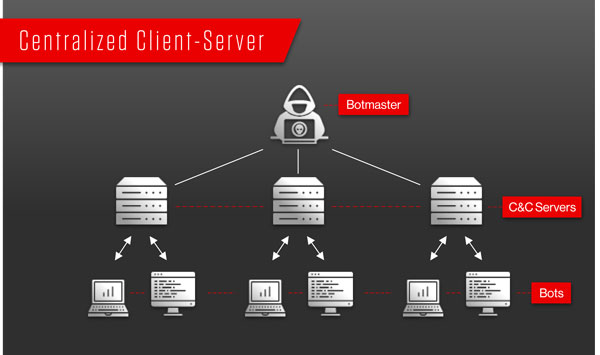
A centralized model with direct communication between the bot herder and each. Botnets that make use of a c&c structure are fairly easy to disable if you can. Botnets are controlled by command and control (c&c) servers, which are computers controlled by hackers or hacker groups that can send commands to botnets in the.
Set your antivirus and antispyware programs to update automatically. Issuing commands is a vital part of controlling a botnet. Up to 18% cash back here are a few steps you should take to protect your systems from botnet infiltration:
Some are more sophisticated than other methods. Here are the most important ways you can detect and prevent botnet attacks on your devices. Patch early, patch often, patch always.
Botnet owners or herders are able to control the machines in their botnet by means of a covert channel such as irc (internet relay chat), issuing commands to perform malicious activities. There are actually various methods the hacker can use to command and control the botnet; How to disable botnets disable a botnet's control centers.
Bot herders control their botnets through one of two structures: A firewall is a security. How to prevent botnet attack?